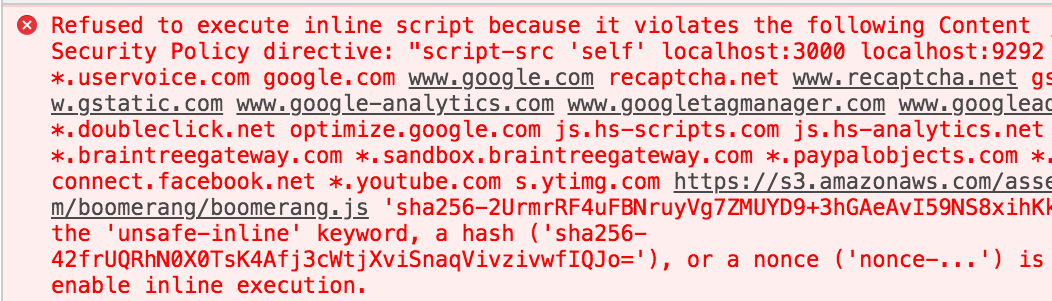
UNSAFE-INLINE and UNSAFE-EVAL
Oleksii Vasyliev, Railsware
Brought to you by Alexey Vasiliev, Railsware
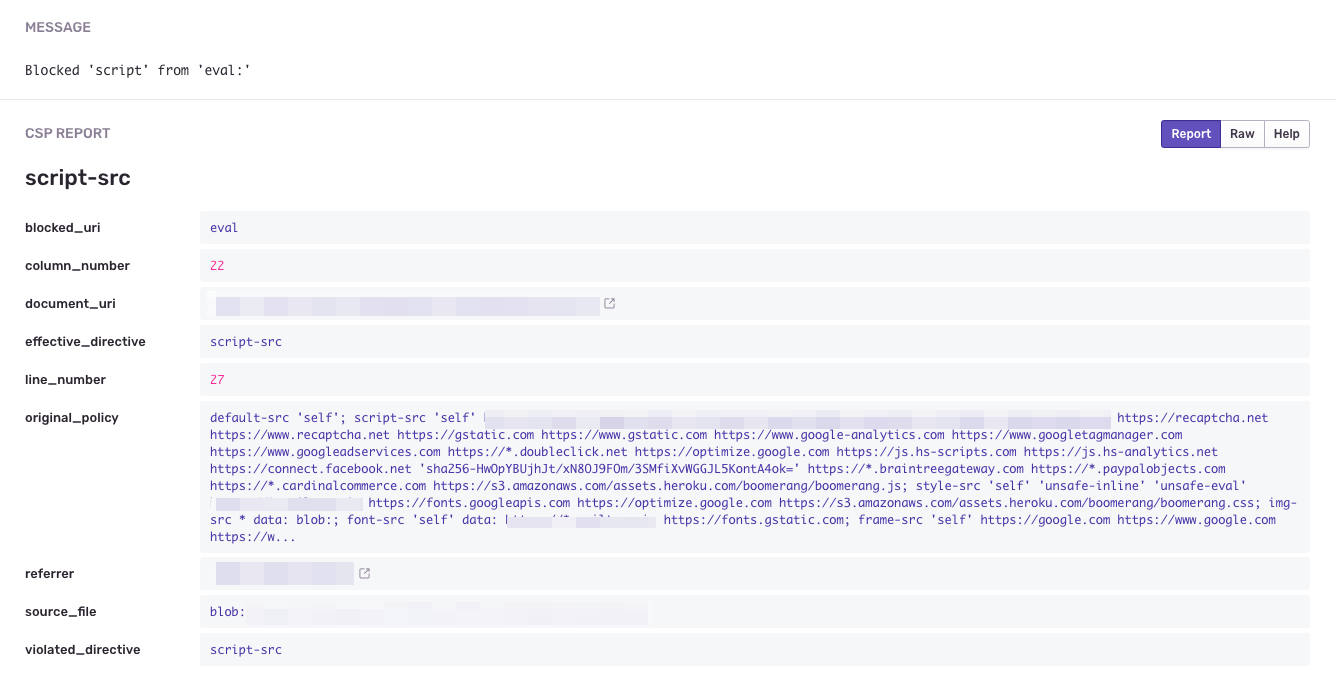
Content-Security-Policy: default-src 'self';
img-src * data: blob:;
media-src media1.com media2.com;
script-src userscripts.example.com
Rails.application.config.content_security_policy do |policy|
policy.default_src :self
policy.script_src :self, 'js.example.com'
policy.style_src :self, :unsafe_inline
policy.report_uri "/csp-violation-report-endpoint"
end
content_security_policy do |policy|
policy.default_src :self
policy.img_src '*', :data, :blob
policy.script_src :self, 'js.example.com'
policy.frame_src :self, 'widget.example.com'
policy.media_src :self, 'media.example.com'
end

Content-Security-Policy-Report-Only: default-src *;
img-src * data: blob:;
report-uri /csp-violation-report-endpoint/
Strict-Transport-Security:
max-age=31536000 ; includeSubDomains; preload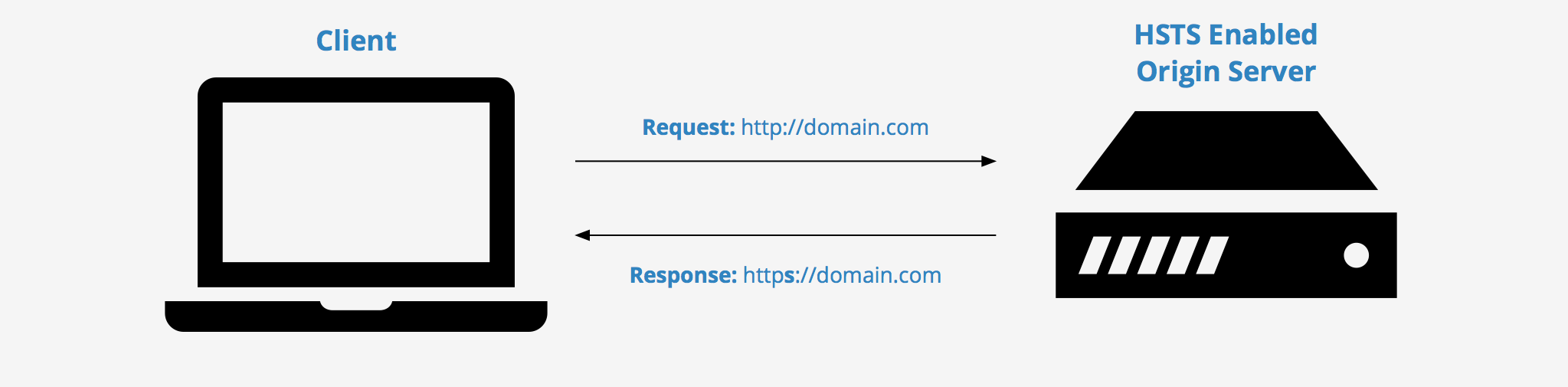
X-Frame-Options: deny | sameorigin | allow-from: DOMAIN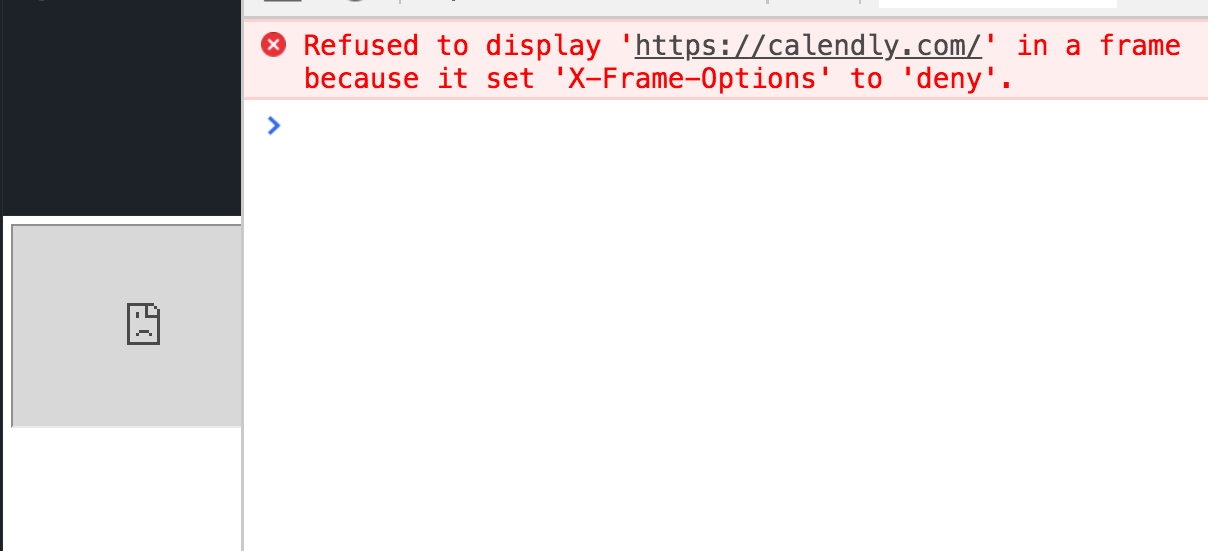
Ask the browser not to cache pages with sensitive information
response.headers['Cache-Control'] =
'private, no-cache, no-store, max-age=0'
response.headers['Pragma'] = 'no-cache'
response.headers['Expires'] = '0'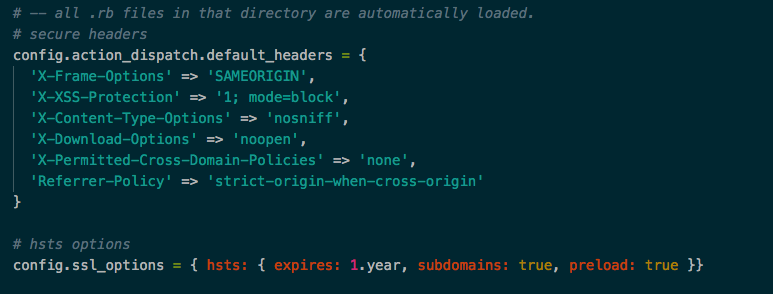
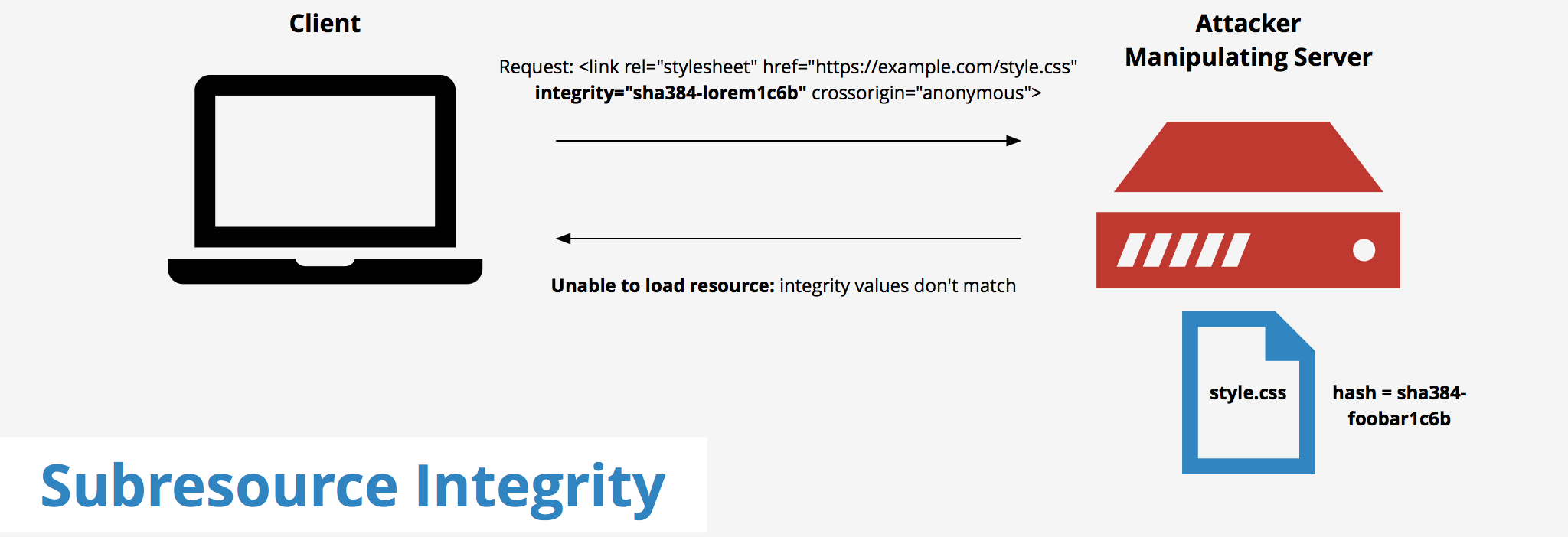
javascript_include_tag :application,
integrity: true, crossorigin: 'anonymous'
<script src="/assets/application.js"
integrity="sha-256-TvVUHzSfftWg1rcfL6TIJ0XKEGrgLyEq6lEpcmrG9qs="
crossorigin="anonymous"></script>

protect_from_forgery with: :exception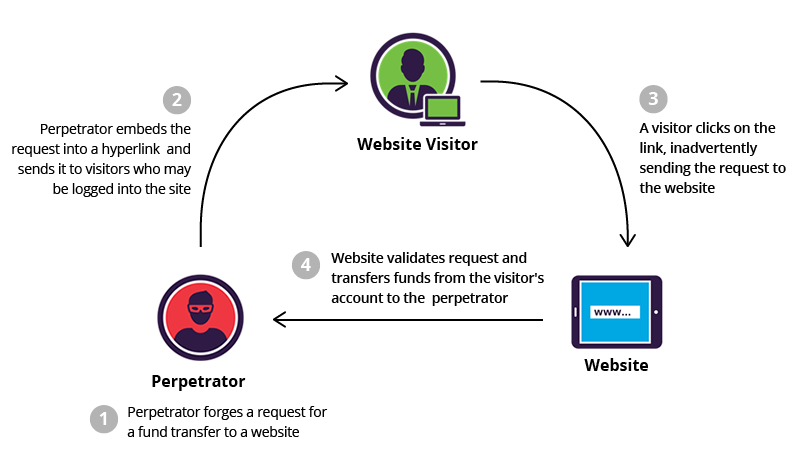
ActiveSupport::SecurityUtils.secure_compare(a, b)$ gem unpack rest-client
Fetching rest-client-2.1.0.gem
Unpacked gem: '/tmp/rest-client-2.1.0'
$ git clone https://github.com/rest-client/rest-client
$ git checkout 2.1.0
$ cp -r /tmp/rest-client-2.1.0 ./rest-client
$ cd rest-client && git diff
My message to companies that think they haven't been attacked is: You're not looking hard enough